| Network Data Source | Custom Network Features |
| Network Data Labeled | Yes |
| Host Data Source | - |
| Host Data Labeled | - |
| Overall Setting | Home IT |
| OS Types | Ubuntu 12.04 LTS Windows 7 iOS Android Misc. Linux |
| Number of Machines | 10 |
| Total Runtime | ~109 hours |
| Year of Collection | 2015 |
| Attack Categories | Various attacks targeting Wi-Fi networks using WEP |
| User Emulation | Yes, presumably synthetic |
| Packed Size | 11,7 GB |
| Unpacked Size | - |
| Download Link | Access must be requested |
Overview
The Aegean WiFi Intrusion Dataset (AWID), named after the university where the authors are located, is a medium-sized collection of traffic collected from a small home Wi-Fi network protected using the deprecated Wired Equivalent Privacy (WEP). Targeting this network, an attacker executes several attacks geared towards WEP specifically, the selection of which is preceded by the authors discussing these kinds of attacks both in a theoretical and practical manner. The distinguishing features of this dataset are its focus on wireless communication, whose structure and patterns naturally differ from that of wired networks, with the general goal being to facilitate research towards security in wireless networks that goes beyond that supplied by the IEEE standard alone. Additionally, the authors showcase the application of several machine learning methods on a subset of this data.
This dataset also seems to be known as AWID2, which is the name it is listed under on its homepage. Since then, the authors have also published a more “modern” version called AWID3, which focuses on less deprecated standards such as WPA2 and Wi-Fi 5.
Environment
Traffic is collected in a physical lab mimicking the structure and scale of a typical home network, hosting laptops, smartphones, smart TVs, and other devices. A full list, including OS versions and details like network cards, is available in Table 5 of the paper. Some devices regularly leave and re-enter the network, while others remain stationary. The network is organized in infrastructure mode (as opposed to Ad-Hoc mode), meaning there is a single Access Point (AP), in the form of a Netgear router. As mentioned, the protection mechanism used is the deprecated WEP.
Traffic is collected by a separate machine not associated with the network using Tshark (the terminal version of Wireshark). The authors note that this method does not guarantee the capturing of all packets, but resembles a cost-efficient and simple way to collect traffic in such an environment. The attacker acts from outside the physical perimeter of the lab and is initially also not associated with the network.
Activity
Benign traffic is generated by devices inside the network performing activities such as web browsing, VoIP, file transfers, or video streaming, although it is not detailed in which manner this behavior is generated/automated. Attacks, as previously mentioned, are motivated by exploiting the weaknesses of WEP, and are grouped into four classes. A full description for each of these attacks can be found in Chapters 3 and 5 of the paper, which additionally also includes attacks against WPA/WPA2, even though they are not included in this dataset:
- Injection attacks
- ARP injection
- Chop-Chop
- Fragmentation
- Flooding attacks
- De-Authentication
- Disassociation
- De-Authentication broadcast
- Disassociation broadcast
- Block acknowledge
- Authentication request
- Fake power saving
- CTS
- RTS
- Beacon
- Probe request
- Probe response
- Impersonation attacks
- Honeypot
- Evil Twin
- Passive attacks (not present in the dataset due to the nature of these attacks)
- FMS
- Korek
- PTW
- Dictionary
These attacks are either executed using existing tools like Metasploit or Aircrack-NG, or are implemented in custom C. Activity is generally divided into segments of one hour, where the first X minutes contain only benign behavior, and the attacker becomes active during the remaining 60-X minutes. For the “Full” datasets (explained in the next section), this ratio is 45 to 15 minutes, for the “Reduced” datasets it is 35 to 25 minutes. The attacker changes their MAC addresses multiple times throughout the data collection period. Details regarding attack sequences are only given for a subset of data, see Section 3.C of the paper.
Contained Data
Every collected packet is processed into a connection record consisting of 156 features (the last of which is the class label). The authors designed this set of features to encompass almost all fields that can appear in an 802.11 frame, resulting in many fields often being empty by design. Rare values like vendor-specific fields, as well as the data field itself, are not considered. A full list of all features can be found on the homepage, features are generally divided into:
- MAC layer information (source address, initialization vector, etc.)
- Radiotap information (like signal strength)
- General frame information (like packet numbers)
All values except for the SSID are given as integers, including hex values, which are transformed accordingly. Data is divided into eight individual datasets, whose characteristics are depicted in the table below (taken directly from the paper):
- First differentiation: “CLS” vs. “ATK”, where the former uses one of the four aforementioned classes as labels, while the latter instead uses the exact attack name. Data is otherwise identical (why didn’t they just include two labels?).
- Second differentiation: “F” (Full) vs “R” (Reduced), with the latter being designed to facilitate processing on weaker machines. It is a separate dataset, not a subset of the former.
- Third differentiation: “Trn” (Training) vs. “Tst” (Testing), as is typical for datasets designed for purposes related to machine learning
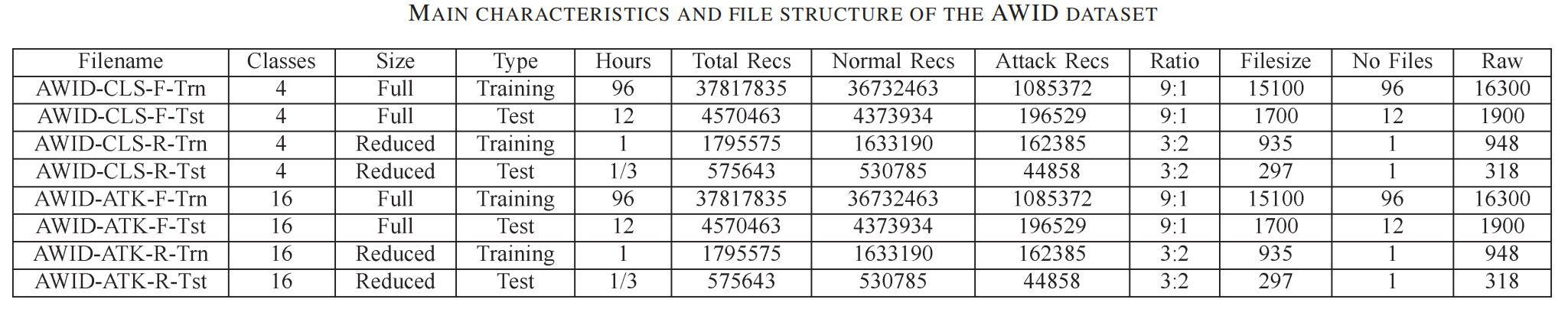
Data is divided into segments each covering one hour of traffic available in CSV format, though there is no header - as mentioned, information about fields have to be sourced from their homepage. The labeling process itself is not detailed.
Papers
Links
Data Examples
Snippet of connection records taken from AWID-ATK-R-Trn.
[...]
0,?,0.000000000,1393664522.061901000,0.011024000,0.011024000,3219.416144000,148,148,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5320983163,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-58,1,0,0x08,0,0,8,0x00,0,0,0,0,0,0,0,ff:ff:ff:ff:ff:ff,ff:ff:ff:ff:ff:ff,28:c6:8e:86:d3:d6,28:c6:8e:86:d3:d6,28:c6:8e:86:d3:d6,0,2094,?,?,?,?,?,?,1,1,0,0x0000,1,0,0,0,0,1,0,0,0,0,0,?,?,?,0x0000003ef7fa1194,100,?,?,?,?,?,?,?,?,?,1,AegeanSecLab,6,1,2,0,0x00,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.073183000,0.011282000,0.011282000,3219.427426000,261,261,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5320993514,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-47,1,0,0x08,0,0,8,0x00,0,0,0,0,0,0,0,ff:ff:ff:ff:ff:ff,ff:ff:ff:ff:ff:ff,b0:48:7a:e2:62:23,b0:48:7a:e2:62:23,b0:48:7a:e2:62:23,0,3190,?,?,?,?,?,?,1,1,0,0x0000,0,1,0,0,0,0,0,0,0,0,0,?,?,?,0x000000002c5aad80,100,?,?,?,?,?,?,?,?,?,1,pnet,6,0,1,0,0x00,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.076250000,0.003067000,0.003067000,3219.430493000,124,124,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5320997676,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-25,1,0,0x28,0,2,8,0x02,0,0,0,0,1,0,314,00:13:33:87:62:6d,00:13:33:87:62:6d,28:c6:8e:86:d3:d6,c0:18:85:94:b6:55,28:c6:8e:86:d3:d6,0,570,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,0xf39468,0,0x8e713a5a,?,?,0,0,0,0x0000,0,?,?,?,0,60,normal
0,?,0.000000000,1393664522.076562000,0.000312000,0.000312000,3219.430805000,40,40,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5320998668,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-32,1,0,0x1d,0,1,13,0x00,0,0,0,0,0,0,0,28:c6:8e:86:d3:d6,?,?,?,?,?,?,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.088660000,0.012098000,0.012098000,3219.442903000,99,99,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321010290,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-25,1,0,0x08,0,0,8,0x00,0,0,0,0,0,0,0,ff:ff:ff:ff:ff:ff,ff:ff:ff:ff:ff:ff,28:c6:8e:86:d3:d6,28:c6:8e:86:d3:d6,28:c6:8e:86:d3:d6,0,885,?,?,?,?,?,?,1,1,0,0x0000,1,0,0,0,0,1,0,0,0,0,0,?,?,?,0x0000000000000000,100,?,?,?,?,?,?,?,?,?,1,AegeanSecLab,6,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,evil_twin
0,?,0.000000000,1393664522.088952000,0.000292000,0.000292000,3219.443195000,54,54,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321011202,0,0,0,0,1,0,0,0,54,2437,0,0,1,1,0,0,0,0,0,0,0,0,-41,1,0,0x24,0,2,4,0x01,0,0,0,0,0,0,44,28:c6:8e:86:d3:d6,28:c6:8e:86:d3:d6,20:64:32:54:c9:da,20:64:32:54:c9:da,28:c6:8e:86:d3:d6,0,483,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.088957000,0.000005000,0.000005000,3219.443200000,40,40,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321011247,0,0,0,0,1,0,0,0,24,2437,0,0,1,1,0,0,0,0,0,0,0,0,-24,1,0,0x1d,0,1,13,0x00,0,0,0,0,0,0,0,20:64:32:54:c9:da,?,?,?,?,?,?,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.102900000,0.013943000,0.013943000,3219.457143000,159,159,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321024039,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-32,1,0,0x08,0,0,8,0x00,0,0,0,0,0,0,0,ff:ff:ff:ff:ff:ff,ff:ff:ff:ff:ff:ff,00:13:33:87:62:6d,00:13:33:87:62:6d,00:13:33:87:62:6d,0,1973,?,?,?,?,?,?,1,1,0,0x0000,1,0,0,0,0,1,0,0,0,0,0,?,?,?,0x000000000abe01bc,100,?,?,?,?,?,?,?,?,?,1,OTE29224e,6,0,1,0,0x00,?,1,2,2,1,2,0,0,0x0000,0x0000,0,0,0,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.133740000,0.030840000,0.030840000,3219.487983000,185,185,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321054677,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-42,1,0,0x08,0,0,8,0x00,0,0,0,0,0,0,0,ff:ff:ff:ff:ff:ff,ff:ff:ff:ff:ff:ff,38:22:9d:ae:c5:65,38:22:9d:ae:c5:65,38:22:9d:ae:c5:65,0,3949,?,?,?,?,?,?,1,1,0,0x0000,1,1,0,0,0,1,0,0,0,0,0,?,?,?,0x0000003ef550d184,100,?,?,?,?,?,?,?,?,?,1,CYTA C565,6,0,1,0,0x00,?,1,2,2,1,2,0,0,0x0000,0x0000,0,0,0,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.139960000,0.006220000,0.006220000,3219.494203000,122,122,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321062199,0,0,0,0,1,0,0,0,54,2437,0,0,1,1,0,0,0,0,0,0,0,0,-41,1,0,0x20,0,2,0,0x01,0,0,0,0,1,0,44,28:c6:8e:86:d3:d6,00:13:33:87:62:6d,20:64:32:54:c9:da,20:64:32:54:c9:da,28:c6:8e:86:d3:d6,0,484,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,0x275e33,0,0x6db9d78a,?,?,?,?,?,?,?,?,?,?,?,60,normal
0,?,0.000000000,1393664522.139966000,0.000006000,0.000006000,3219.494209000,40,40,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321062253,0,0,0,0,1,0,0,0,24,2437,0,0,1,1,0,0,0,0,0,0,0,0,-25,1,0,0x1d,0,1,13,0x00,0,0,0,0,0,0,0,20:64:32:54:c9:da,?,?,?,?,?,?,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.141447000,0.001481000,0.001481000,3219.495690000,122,122,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321062896,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-25,1,0,0x20,0,2,0,0x02,0,0,0,0,1,0,314,00:13:33:87:62:6d,00:13:33:87:62:6d,28:c6:8e:86:d3:d6,20:64:32:54:c9:da,28:c6:8e:86:d3:d6,0,484,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,0x56a552,0,0x674d2a13,?,?,?,?,?,?,?,?,?,?,?,60,normal
0,?,0.000000000,1393664522.141764000,0.000317000,0.000317000,3219.496007000,40,40,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321063872,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-33,1,0,0x1d,0,1,13,0x00,0,0,0,0,0,0,0,28:c6:8e:86:d3:d6,?,?,?,?,?,?,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.143722000,0.001958000,0.001958000,3219.497965000,338,338,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321065923,0,0,0,0,1,0,0,0,54,2437,0,0,1,1,0,0,0,0,0,0,0,0,-41,1,0,0x20,0,2,0,0x01,0,0,0,0,1,0,44,28:c6:8e:86:d3:d6,00:13:33:87:62:6d,20:64:32:54:c9:da,20:64:32:54:c9:da,28:c6:8e:86:d3:d6,0,485,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,0x285e33,0,0xfdd0570c,?,?,?,?,?,?,?,?,?,?,?,276,normal
0,?,0.000000000,1393664522.143727000,0.000005000,0.000005000,3219.497970000,40,40,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321066009,0,0,0,0,1,0,0,0,24,2437,0,0,1,1,0,0,0,0,0,0,0,0,-25,1,0,0x1d,0,1,13,0x00,0,0,0,0,0,0,0,20:64:32:54:c9:da,?,?,?,?,?,?,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.146961000,0.003234000,0.003234000,3219.501204000,338,338,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321066672,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-25,1,0,0x20,0,2,0,0x02,0,0,0,0,1,0,314,00:13:33:87:62:6d,00:13:33:87:62:6d,28:c6:8e:86:d3:d6,20:64:32:54:c9:da,28:c6:8e:86:d3:d6,0,485,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,0x522809,0,0x496651db,?,?,?,?,?,?,?,?,?,?,?,276,normal
0,?,0.000000000,1393664522.147272000,0.000311000,0.000311000,3219.501515000,40,40,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321069376,0,0,0,0,1,0,0,0,1,2437,0,1,0,1,0,0,0,0,0,0,0,0,-33,1,0,0x1d,0,1,13,0x00,0,0,0,0,0,0,0,28:c6:8e:86:d3:d6,?,?,?,?,?,?,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.154645000,0.007373000,0.007373000,3219.508888000,54,54,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321076820,0,0,0,0,1,0,0,0,5.5,2437,0,1,0,1,0,0,0,0,0,0,0,0,-56,1,0,0x24,0,2,4,0x01,0,0,0,0,0,0,258,28:c6:8e:86:d3:d6,28:c6:8e:86:d3:d6,3c:5a:37:8c:9a:41,3c:5a:37:8c:9a:41,28:c6:8e:86:d3:d6,0,2795,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.154903000,0.000258000,0.000258000,3219.509146000,40,40,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321077064,0,0,0,0,1,0,0,0,2,2437,0,1,0,1,0,0,0,0,0,0,0,0,-30,1,0,0x1d,0,1,13,0x00,0,0,0,0,0,0,0,3c:5a:37:8c:9a:41,?,?,?,?,?,?,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
0,?,0.000000000,1393664522.155221000,0.000318000,0.000318000,3219.509464000,54,54,0,0,0,0,26,1,1,1,1,0,1,0,0,0,0,0,1,0,0,1,0,0,0,0,0x00000000,0,0,0,5321077396,0,0,0,0,1,0,0,0,5.5,2437,0,1,0,1,0,0,0,0,0,0,0,0,-55,1,0,0x24,0,2,4,0x01,0,0,0,0,0,0,258,28:c6:8e:86:d3:d6,28:c6:8e:86:d3:d6,3c:5a:37:8c:9a:41,3c:5a:37:8c:9a:41,28:c6:8e:86:d3:d6,0,2796,?,?,?,?,?,?,1,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,?,normal
[...]