friTap Documentation¶

SSL/TLS Traffic Analysis Made Simple
Real-time key extraction and traffic decryption for security research
Quick Start¶
# Install friTap
pip install fritap
# Basic usage - Desktop application
sudo fritap --pcap capture.pcap firefox
# Mobile application analysis
fritap -m -k keys.log com.example.app
What is friTap?¶
friTap is a powerful cybersecurity research tool that simplifies SSL/TLS traffic analysis by automating key extraction and traffic decryption. Built on the Frida dynamic instrumentation framework, friTap enables security researchers to analyze encrypted network communications in real-time across multiple platforms.
Key Capabilities¶
- Real-time Key Extraction: Automatically extract TLS keys as they're generated
- Live Traffic Decryption: Decrypt and save TLS payload as PCAP files
- Multi-Platform Support: Works on Linux, Windows, macOS, Android, and iOS
- Extensive Library Support: Supports OpenSSL, BoringSSL, NSS, GnuTLS, WolfSSL, and more
- Pattern-Based Hooking: Hook stripped libraries without symbols
- Advanced Analysis: Bypass anti-analysis techniques and SSL pinning
Use Cases¶
- Malware Analysis: Decrypt C&C communications and data exfiltration
- Privacy Research: Analyze application data transmission practices
- Security Testing: Validate SSL/TLS implementations and configurations
- Digital Forensics: Recover encrypted network communications
- Application Analysis: Understand how applications handle secure communications
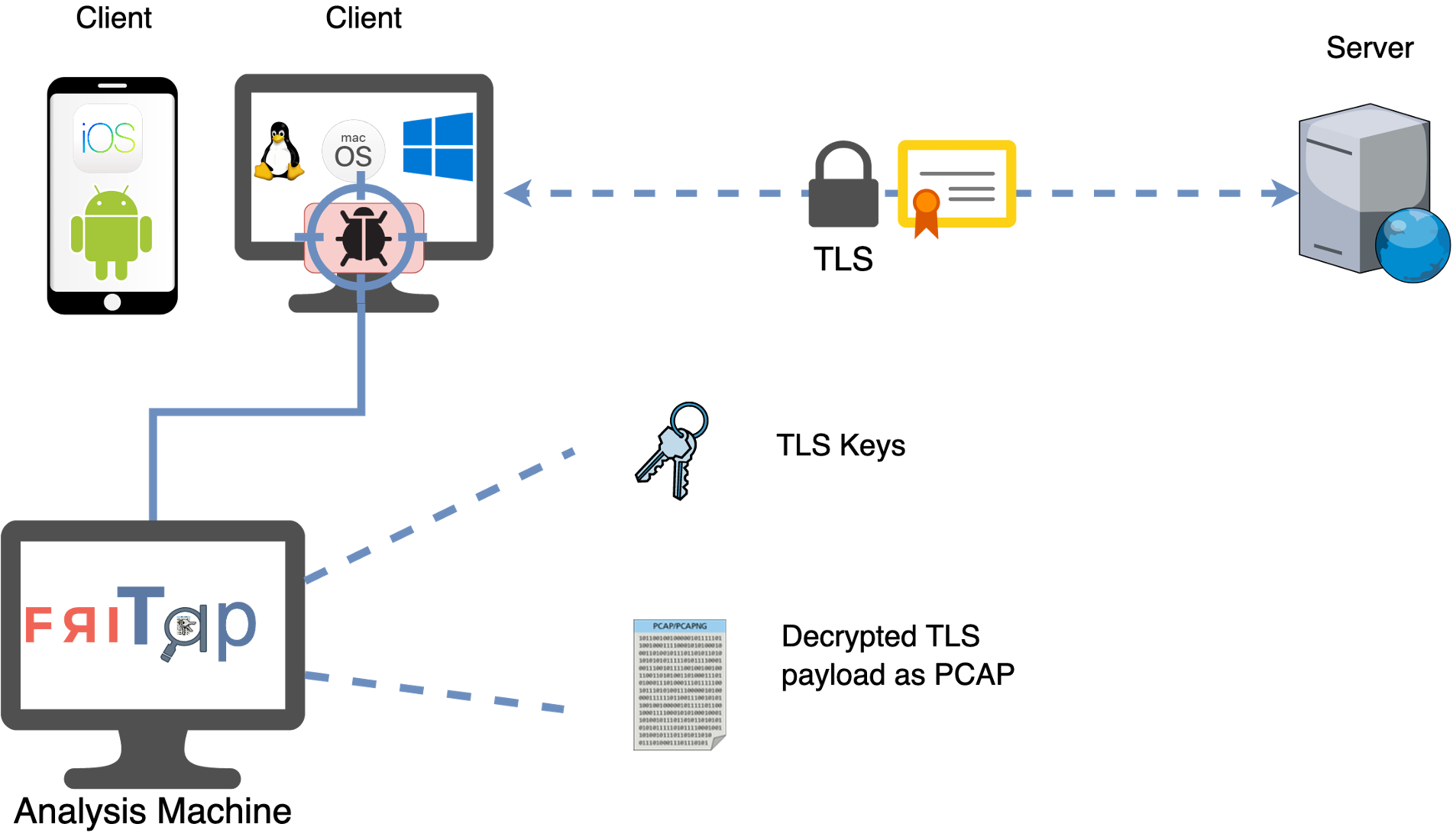
How It Works¶
friTap uses dynamic instrumentation to intercept SSL/TLS operations at the library level:
- Library Detection: Automatically identifies the SSL/TLS library used by the target application
- Hook Injection: Dynamically hooks key functions (read, write, key generation)
- Data Extraction: Captures plaintext data and encryption keys in real-time
- Output Generation: Saves results as PCAP files or key logs for analysis
Supported Platforms & Libraries¶
| Library | Linux | Windows | macOS | Android | iOS | Key Features |
|---|---|---|---|---|---|---|
| OpenSSL | ✓ Full | R/W | TBI | ✓ Full | TBI | Most widely used |
| BoringSSL | ✓ Full | R/W | Keys | ✓ Full | Keys | Google's OpenSSL fork |
| NSS | ✓ Full | R/W | TBI | Keys | TBI | Mozilla's library |
| GnuTLS | R/W | R/W | TBI | ✓ Full | TBI | GNU project library |
| WolfSSL | R/W | R/W | TBI | ✓ Full | TBI | Embedded/IoT focused |
| mbedTLS | R/W | R/W | TBI | ✓ Full | TBI | Lightweight library |
| Schannel | ✗ | ✓ Full | ✗ | ✗ | ✗ | Windows native SSL/TLS |
| Conscrypt | TBA | TBA | TBA | ✓ Full | TBA | Android system SSL |
| S2N-TLS | ✓ Full | ✗ | TBA | ✓ Full | ✗ | AWS library |
| RustTLS | Keys | TBI | TBI | Keys | TBI | Rust implementation |
Legend: - ✓ Full: Complete support (keys + traffic decryption) - R/W: Read/Write hooks only (traffic without keys) - Keys: Key extraction only - TBI: To Be Implemented - TBA: To Be Analyzed - ✗ N/A: Not applicable to platform
Getting Started¶
Prerequisites¶
- Python 3.7+
- Frida 16.0+ (new changes will only work on frida >=17)
- Administrative privileges (for desktop applications)
- ADB access (for Android analysis)
Installation¶
Basic Examples¶
Documentation Sections¶
Getting Started¶
Installation, setup, and basic concepts to get you up and running quickly.
Usage Examples¶
Comprehensive examples for different platforms and use cases with real-world scenarios.
Platform Guides¶
Detailed guides for Android, iOS, Linux, Windows, and macOS analysis.
Advanced Features¶
Pattern-based hooking, spawn gating, anti-detection techniques, and custom scripts.
API Reference¶
Complete API documentation for Python integration and CLI usage.
Troubleshooting¶
Solutions for common issues, debugging techniques, and performance optimization.
Community & Support¶
- GitHub: fkie-cad/friTap
- Email: daniel.baier@fkie.fraunhofer.de
- Research: OSDFCon Webinar
- Blog: Technical Deep Dive
License¶
friTap is released under the GPL v3 License.
Inspired by SSL_Logger and developed by Fraunhofer FKIE CAD